| REMOTE DESKTOP | |
| SUPPORT SERVICE | |
| New PC OS Setup | |
| New Antivirus setup | |
| MS Office installation | |
| Peripheral Setup | |
| Antivirus Removal | |
| PC Optimization | |
| Router Configuration | |
| Data transfer | |
| PC Trobleshooting | |
| Tablet setup | |

VPN (Virtual Private Network)
1. What is VPN?
2. What are the key benefits of VPN technology?
3. What are security measures available with VPN?
4. How CompuMate can help you with VPN technology?
2. What are the key benefits of VPN technology?
3. What are security measures available with VPN?
4. How CompuMate can help you with VPN technology?
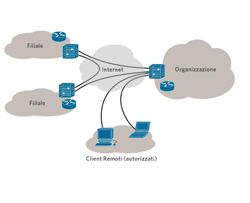 A virtual private network (VPN) helps organizations securely and cost-effectively extends connectivity and improves speed.
A virtual private network (VPN) is a network that uses a public telecommunication infrastructure, such as the Internet, to provide
remote offices or individual users with secure access to their organization's network. It aims to avoid an expensive system of
owned or leased lines that can only be used by one organization. The goal of a VPN is to provide the organization with the same,
secure capabilities, but at a much lower cost. It encapsulates data transfers between two or more networked devices not on the
same private network so as to keep the transferred data private from other devices on one or more intervening local or wide area
networks. There are many different classifications, implementations, and uses for VPNs.
A virtual private network (VPN) helps organizations securely and cost-effectively extends connectivity and improves speed.
A virtual private network (VPN) is a network that uses a public telecommunication infrastructure, such as the Internet, to provide
remote offices or individual users with secure access to their organization's network. It aims to avoid an expensive system of
owned or leased lines that can only be used by one organization. The goal of a VPN is to provide the organization with the same,
secure capabilities, but at a much lower cost. It encapsulates data transfers between two or more networked devices not on the
same private network so as to keep the transferred data private from other devices on one or more intervening local or wide area
networks. There are many different classifications, implementations, and uses for VPNs.Benefits - Securely Connecting Offices, Users and Partners
A VPN (virtual private network) is a private network constructed within a public network infrastructure, such as the global Internet. Businesses can use a VPN to securely connect remote offices and remote users using cost-effective, third-party Internet access, instead of expensive, dedicated WAN links or long-distance remote dial links. Organizations can use a VPN to reduce WAN bandwidth costs, while increasing connectivity speeds by using high-bandwidth Internet connectivity, such as DSL, Ethernet, or cable. A VPN provides the highest possible level of security through encrypted IP Security (IPsec) or Secure Sockets Layer (SSL) VPN tunnels and authentication technologies. These protect data traversing the VPN from unauthorized access. Companies can take advantage of the easy-to-provision Internet infrastructure of the VPN to quickly add new sites or users. They can also dramatically increase VPN reach without significantly expanding infrastructure.
Security Mechanisms & Measures with VPN Technology
Secure VPNs use cryptographic tunneling protocols to provide confidentiality by blocking intercepts and packet sniffing, allowing sender authentication to block identity spoofing, and provide message integrity by preventing message alteration.
Secure VPN protocols include the following :
IPsec (Internet Protocol Security) was originally developed for IPv6, which requires it. This standards-based security protocol is also widely used with IPv4. L2TP frequently runs over IPsec. Transport Layer Security (SSL/TLS) can tunnel an entire network's traffic, as it does in the OpenVPN project, or secure an individual connection. A number of vendors provide remote access VPN capabilities through SSL. An SSL VPN can connect from locations where IPsec runs into trouble with Network Address Translation and firewall rules. However, SSL-based VPNs use Transmission Control Protocol (TCP) and so may be vulnerable to denial-of-service attacks because TCP connections do not authenticate. Datagram Transport Layer Security (DTLS) is used in Cisco's next-generation VPN product, Cisco AnyConnect VPN, to solve the issues SSL/TLS has with tunneling TCP over TCP. Microsoft's Microsoft Point-to-Point Encryption (MPPE) works with their PPTP and in several compatible implementations on other platforms. Microsoft introduced Secure Socket Tunneling Protocol (SSTP) in Windows Server 2008 and Windows Vista Service Pack 1. SSTP tunnels Point-to-Point Protocol (PPP) or L2TPtraffic through an SSL 3.0 channel. MPVPN (Multi Path Virtual Private Network). Regular Systems Development Company owns the registered trademark "MPVPN". Secure Shell (SSH) VPN - - OpenSSH offers VPN tunneling to secure remote connections to a network or inter-network links. This should not be confused with port forwarding. OpenSSH server provides limited number of concurrent tunnels and the VPN feature itself does not support personal authentication.
Authentication
Tunnel endpoints must authenticate before secure VPN tunnels can establish. User-created remote access VPNs may use passwords, biometrics, two-factor authentication or other cryptographic methods. Network-to-network tunnels often use passwords or digital certificates, as they permanently store the key to allow the tunnel to establish automatically and without intervention.
A VPN Extends Security for Remote Users
An SSL VPN and an IPsec VPN have become the primary VPN solutions for connecting remote offices, remote users, and business partners, because they: Provide secure communications with access rights tailored to individual users, such as employees, contractors, or partners Enhance productivity by extending corporate network and applications, Reduce communications costs and increases flexibility.
The two types of encrypted VPNs are:
Site-to-Site IPsec VPN: This alternative to Frame Relay or leased-line WANs allows businesses to extend network resources to branch offices, home offices, and business partner sites. Remote-Access VPN: This extends almost any data, voice, or video application to the remote desktop, emulating the main office desktop. A remote-access VPN may be deployed using SSL VPN, IPsec or both, depending on deployment requirements.
CompuMate @ VPN technology
yes , we can Securely Connect your different Offices in various locations together using VPN technology , also with the moving executives, users and even with your business Partners. So that wherever you are - you are always connected with your office and your people and your business. You are always inside!!!
| Next Step |
To discuss how Compumate Support Services
could benifit your business, please contact us
could benifit your business, please contact us
And if you'd like to know more about how we support our
clients, just call or mail us;
Call : +971 4 4344200
Mail us : sales@compumate.ae